The costliest type of Cyber Security attack in 2020 was Business Email Compromise, otherwise known as BEC. The estimated cost to businesses in 2020 was over $1.8 billion! While it is by far the costliest cybercrime, it is also extremely easy to prevent.
The Attack
BEC attacks are relatively simple to perform and rely heavily on social engineering. The basic premise is a bad actor creates an email that looks legit but has the sole purpose of tricking the recipient into providing information. Oftentimes, the attacks come in the form of impersonating an executive or imitating a legitimate portal that is used by the organization. If the recipient responds or clicks the links in the email, the bad actor may be able to gather important information that furthers their scheme, which typically results in monetary gain.
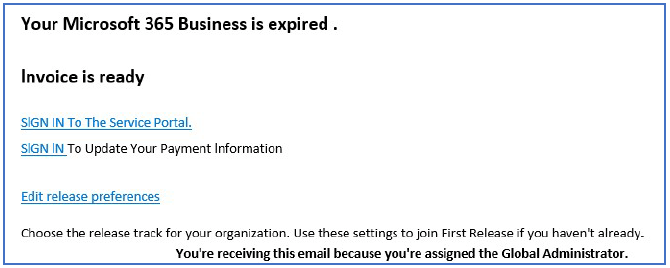
Fake email example
Employees at any level can be targeted, but most often, it’s the management of a company that criminals are really after. The attacker might use a free email service to create an account that mimics an executive’s personal email address. Then use it to try to trick employees to divert payments to the criminal’s bank account.
Another common tactic is to imitate legitimate cloud portals the company uses to conduct its business.
In these attacks, the criminals create a very legitimate-looking email with a link to the portal. The email portion of the deceit may be to pay an invoice or access Accounts Receivable. The portal portion of the deceit is a well-imitated recreation of the legitimate portal. Its sole purpose, however, is to gather valid login information. As soon as the recipient enters their username and password, the criminals have the information they sought.
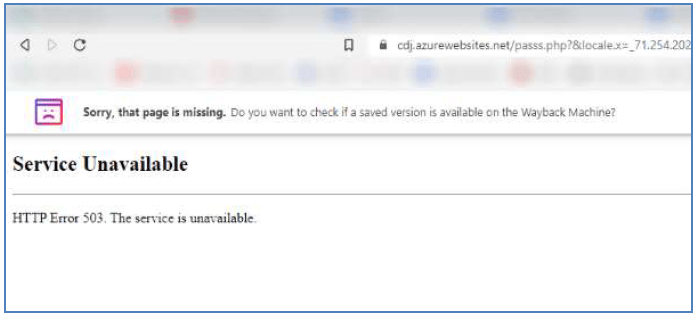
Result of entering credentials for fake portal.
Prevention Strategies
The whole attack is very simple to create, very easy to trick unsuspecting users and very effective; it is also extremely easy to prevent. An effective protection strategy employs a combination of end user training and technology. The technology can mitigate the risk pretty significantly, but end user training is the real key. Knowledgeable employees are far more likely to recognize the social engineering tactic and question an email’s legitimacy before taking any action.
SelecTech has found that a combination of 3) Effective Spam Protection, 2) Multi-Factor Authentication and 1) End User Training eliminates the possibility of falling victim to Business Email Compromise.

