Phishing schemes are getting more elaborate these days. Employing social engineering techniques that can fool even the savviest person. Recently, I received an email that looked extremely legit when glanced at quickly, but closer inspection revealed tell-tale signs of phishing.
The email proceeded to explain that my Apple ID was locked because of suspicious activity. Listing a date, platform, and even the location of where the breach occurred. That all seems like extremely legit information, and it is but for more reasons than one.
First, it certainly makes you quickly think, “whoa, someone logged into my account?” Then just as quickly, it hits me… I have Two-Factor Authentication turned on, why didn’t I receive the approval request on my devices.
Strike one for the bad guys.
Two, the errors in the email itself (look below and you’ll notice yourself what I mean) further exploit the email as a phishing scheme. Apple does not use contractions in their emails, the main subject starts with “We’ve”, an official Apple correspondence would have used “We have”, next in the sentence is the section “sign-in to a iCloud via a web browser on Chrome.”
In other words, someone signed into some sort of iCloud, not iCloud per se, but some form of iCloud, and used a browser on Chrome? I thought Chrome was the browser? Perhaps they meant Chromebook?
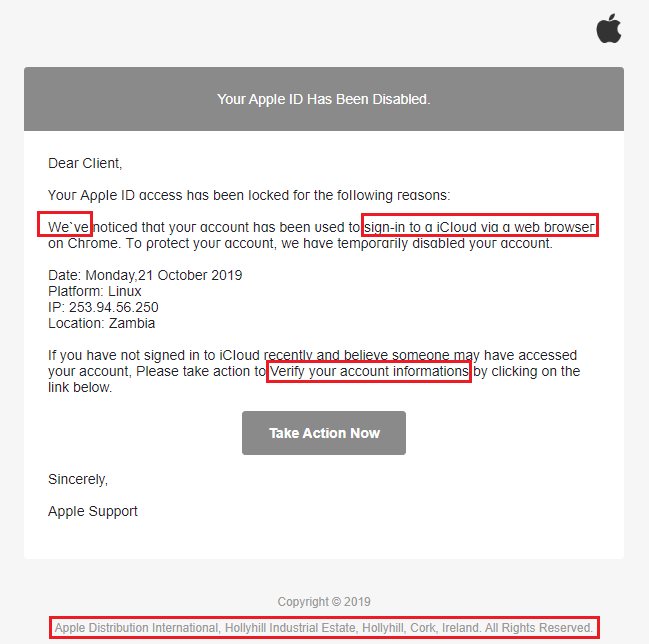
Next up in the email, I need to verify my “informations”, what exactly does that mean? Plus, why does “verify” have a capital “V”? Does that make it more important?
Moving on, we should click the link “Take Action Now” and somehow fix it through LinkedIn because that is where the link takes you. Obviously, a hijacked location on LinkedIn!
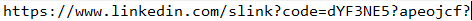
Then there is the Apple location at the bottom of the email.

The Hollyhill location? Really? While that site does provide customer care, it also does finance, localization, logistics, manufacturing, finance, sales support, and transport management. If they were supporting this type of customer care, I’m pretty sure that section would have just said “Copyright © 2019 Apple Inc. One Apple Park Way, Cupertino, CA 95014 USA. All rights reserved.” And included links for the Apple ID, Support, and their Privacy Policy none of which were present in the phishing email.
For the more technically inclined, checking the message header revealed the email came from a domain not associated with apple at all “asupriyadilas.com”.
Another good example is the Office 365 phishing email.
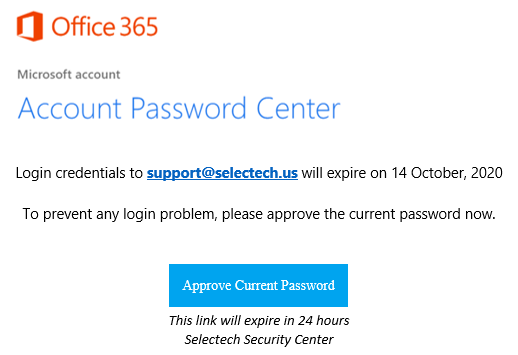
The email does look like a legit Microsoft email but there are mistakes that can be found. The email eludes to your password expiring in the next day, this makes it seem important and urgent. But this is an attempt to steal your password and gain access to your account. You may ask, “why are they only asking for the password?” It is because they already know your email/username. Now, the phishing email provides two pieces of information. One being the account is live and someone is using it, and two being your password if you fall victim to the phishing scheme.
Here is a quick recap of what to do and what NOT to do when receiving an email that deals with any type of online account. Remember phishing emails try to convince you that some suspicious activity occurred in order to get you to click on their links:
- NEVER EVER click the links! No matter how tempting.
- Inspect the email for legitimacy, are contractions used, proper sentence structure, etc.
- If you already know that you have additional security enabled, did you receive any type of message, code, approval request from that mechanism during the date and time indicated in the email?
- Hover over links and see where they lead (but NEVER click them).
- Always go to the source to verify your account. For example, if the email is about your Apple ID, go to https://appleid.apple.com the official Apple ID site. If the email is about Office 365 go to https://portal.office.com that lands you at the official Microsoft login.
If you clicked on the link and entered information, access that specific account immediately and change your password. If you use the same password at multiple sites with the same email/password combination change your passwords immediately and configure Two-Factor authentication if and where possible.
If you believe more personal information was exposed, such as your Social Security number, credit card, bank account numbers, and other personally identifiable information go to IdentityTheft.gov and provide the information requested.
If you believe your system is compromised or need technical assistance for your network contact SelecTech, Inc to learn how we can help @ 717-774-2018.
