PLEASE READ THIS IMPORTANT ARTICLE FULLY. THE NEXT TWO MINUTES MAY SAVE YOU HOURS IN LOST PRODUCTIVITY.
As you may or may not know, there has been an increase in phishing attempts specifically aimed at Microsoft 365 subscribers. You can reference an article on our blog regarding the topic: https://selectech.us/looks-legit/
Recently, we’ve had customers who have fallen victim to phishing emails. These emails were so well crafted that it would fool anyone. There is nothing to be ashamed of by being a victim of these attacks. They are very stealthy and very deceptive and can be very dangerous. These emails were so well crafted that when the email was received it usually included some verbiage that was more personal than normal.
For example, one individual received an email suggesting he was receiving a payment. Thing was, while we have all received these types of emails, this one was personal in the sense that he was expecting a payment from the exact individual he was receiving the email from, which made it all that more believable.
After the individual clicked on the document that was attached it landed him on a page that was identical to Microsoft 365. On that page, he put in his credentials and submitted the information thinking he was logging in to access the document, then nothing!
That’s when he knew he was had.
The goal of the phishing email was accomplished, that goal was to capture his credentials. Not long after this occurred his account was logged into by an unknown party originating in South Africa who then used his account to send additional phishing emails to hundreds of his contacts. And, because these emails were being sent from his account each email had his official email signature making the emails look genuine, when in fact they were not.
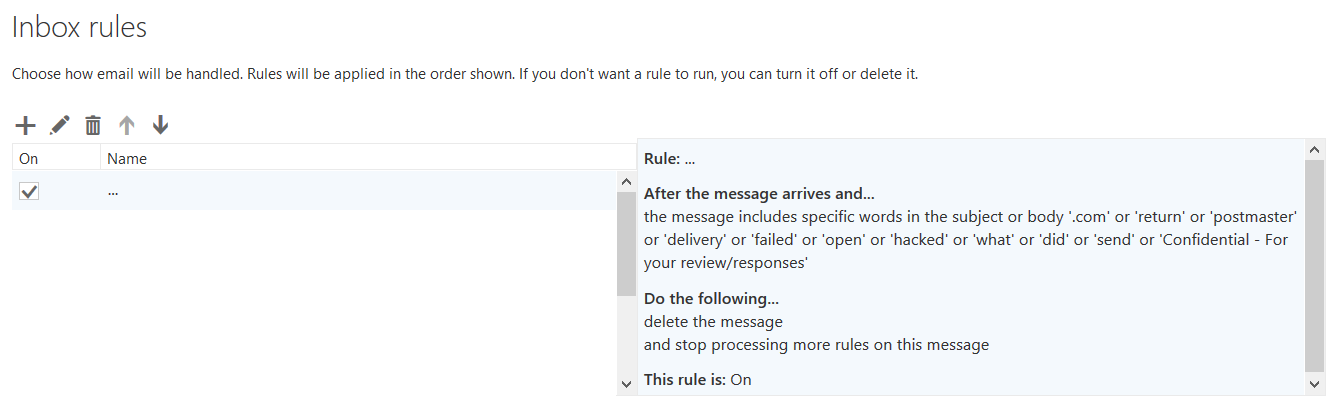
To make matters worse, the attacker created a rule in the inbox that would send all the email that would be received in the inbox to the deleted items folder and eventually delete the emails.
In addition, the attacker actively monitored emails coming back from any recipient that replied to the phishing email asking if the email was legit. In these replies, the attacker would basically suggest that it was legit simply to get the end user to open the attachment.
The attack was halted by taking specific actions, changing passwords, removing the rule, forcing a logoff of all active sessions, and more importantly enabling Multi-Factor Authentication.
Fortunately, Microsoft has provided us with some built-in protection that we HIGHLY RECOMMEND for your security and sanity. That protection is in the form of Multi-Factor Authentication (MFA).
Here is how it works. After being enabled, each user must log in to the Microsoft 365 portal. There, the user will be prompted with an option to get started with multi-factor authentication. Further, into the wizard, they will have to provide a phone number to either receive a call or text from Microsoft. The call or text contains a code which they will have to enter to enable the Multi-Factor Authentication.
Thereafter, the Multi-Factor Authentication will only be required when a user logs into the Microsoft 365 portal. After they enter their username and password, a text or phone call will be received on the number specified above with a random code. The user enters the code and they are granted access.
It may seem like a bit of a pain to get setup, but believe me, it will take much more time to sort through your email being compromised without this protection.
I was asked by the individual after the issue was resolved on why the attacker would simply send so many emails. It seemed like a waste of time for someone to gain someone’s credentials to simply send more emails.
The answer is simple, the phishing email completes two tasks,
- Gets you to leak your private information – hence your username and password for the specific service.
- Keep you busy fighting the current issue at hand – your compromised account.
His next questions, was what good does that do. The answer is even more simple than you would expect. During the time an individual is fighting an attack on a compromised account, the attacker is attempting to use that username/password combination on hundreds of other sites through automated tools. Because, more likely than not the same username/password combination has been used elsewhere.
I’m sure you can imagine what would happen if an attacker was successful in compromising other sites using a username/password combination that was the same across many sites.
If you would like additional information, have questions, or if would like us to enable Multi-Factor Authentication for your users we are here to assist. Please contact SelecTech @ 717-774-2018